Phishing & Vhishing 🎣
Vhishing attacks are carried out over the phone
- Never give remote access to your computer to anyone who phones you
- Never connect to a website if advised by the caller this more than likely will be an attempt to download malware onto your computer or take remote control of it.
- Never give personal, bank or login information over the phone or input them on a website unless you can verify that the caller or website is genuine.
- If you do give access to your computer notify ITD as soon as possible also you will need to contact your service providers such as your bank, Credit Card Company and mobile phone provider and advise them that your details maybe compromised.
- Please note that ITD will never ask for login details by email.
Phishing attacks can take many forms, but they all share a common goal – getting you to share sensitive information with a third-party. Even though ITD has systems in place to help protect against this type of attack. There is no guarantee that all attacks will be detected and stopped.
Responding to a phishing email, and providing your UL username and password will not only disrupt your email access and personal security, but potentially has serious consequences for the University – such as blacklisting of our email servers causing email bounce backs affecting other users and can also cause reputational damage and data protection concerns. In addition, dealing with phishing attacks places significant demands on ITD, and resources which would be normally assigned to strategic projects have to be reassigned to deal with the impact of these incidents.
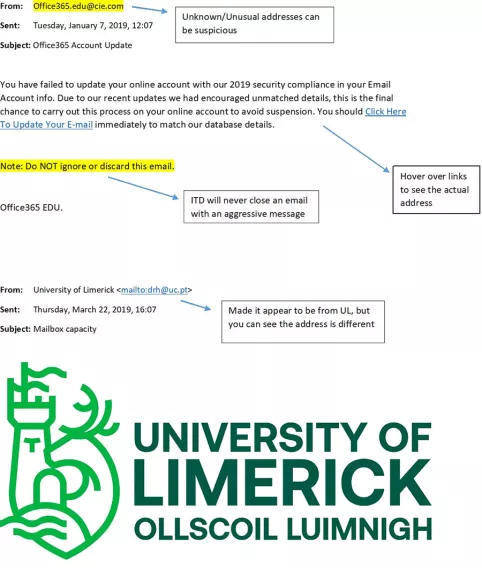
- Check for spelling mistakes
- Don’t trust the display name. Check the email address header – do not open the email if it looks suspicions
- Look but don’t click – Hover you mouse over any links and check if you recognise the link
- Be particularly suspicious of any email using threatening or urgent language
- ITD will never send you an email looking for your password or to verify your email account.
One of the best forms of defense against these types of attacks is user vigilance and awareness.
Here are some simple things you can do to help avoid a Phishing type attack:
- Do not share your Computer Account Password with anyone
- Be careful of emails requesting you to verify your login details. ITD will never ask you to do this over email
- Do not click on links or attachments from senders that you do not recognise
- Do not provide any sensitive personal information over email • Watch for email senders that use suspicious or misleading domain names
- If you are unsure an email is legitimate DO Not Open It! Contact ITD at the earliest opportunity
- Be wary of phone calls claiming to be from help desks especially if they request to go to a website
- Ensure your device is running an up to date anti-virus application and your operating system is fully patched.
- Do not register your UL address on numerous external sites, websites, forums or email distribution lists - except those for University related purposes
- If you suspect your account has been compromised contact ITD and change your account password immediately using UL’s Self-Service Password Reset Portal (Reset Password | University of Limerick (ul.ie)
- Do not click any links
- Do not open any attachments
- Do not enter any personal details on the fraudulent email or website.
- Report the ’phishing’ email to the ITD
- Delete the email.
Report the issue to ITD, disconnect your devices from the network and reset your password using the following link:
Malware 🛡️
Malware is software designed to cause damage to a computer, server or computer network.
- Viruses
This is one of the oldest and most common forms of malware. A computer virus modifies files on a computer in such a way that when a legitimate file is executed, the virus is also executed. Viruses are hard to clean up because they are executed from legitimate programs. To help prevent viruses attacking your computer it is essential that you have a recognised anti-virus program running on your computer and that it is updated regularly. - Worms
The main difference between a virus and a worm is that the worm has the ability to self-replicate. Unlike computer viruses a worm can spread to other systems and networks without end-user action. Having an up-to-date anti-virus application will help protect your computer from worms. - Ransomware
These are malware programs that encrypt your data and hold it for ransom. Over the last few years this type of malware has become very common and sophisticated. Social engineering techniques are used to trick victims into downloading the ransomware. The best defense against ransomware attacks is to backup your files regularly. Under no circumstances should you pay a ransom if your computer is affected as there is no guarantee you will get your data released. - Fileless malware
Traditional malware travels and infects new systems using files on the compromised computer. Fileless malware doesn’t directly use files or the file system. Instead it resides in the computer’s memory and is spread from there. As this malware resides in memory it makes it more difficult for anti-virus applications to detect it. - Trojans
Trojans masquerade as legitimate programs, but they contain malicious code. A Trojan is generally executed by some action initiated by the victim. Trojans can be delivered as attachments in email on by users visiting sites that contain malicious software. Having an up-to-date anti-virus application will help protect your computer from Trojans. Caution should also be taken when visiting unfamiliar websites. - Adware/Spyware
Spyware on the other hand are programs that harvest information from your computer. This can include browsing habits and even key strokes. One emerging threat from spyware is the information harvested from the computer can be used in other types of attacks that require a level of social engineering.
These can be introduced to a computer by several means for example:
- Connecting an infected external drive to your machine (USB memory stick or external hard drive)
- Downloading an infected file from the Internet
- Clicking on a link supplied in a phishing email
- Downloading and opening an infected email attachment.
Ransomware 🌐
Ransomware is a type of malware that prevents or limits users from accessing their system, either by locking the system's screen or by locking the users' files unless a ransom is paid.
These can be introduced to a computer by several means for example:
- Connecting an infected external drive to your machine (USB memory stick or external hard drive)
- Downloading an infected file from the Internet
- Clicking on a link supplied in a phishing email
- Downloading and opening an infected email attachment.
If you suspect that you pc/laptop has been targeted by ransomware immediately disconnect it from the network and contact ITD Service desk.
Spyware 💻
Adware is unwanted software designed to push advertisements up on your screen, most often within a web browser.
Spyware on the other hand are programs that harvest information from your device. This can include browsing habits and even key strokes. Often this information is passed on to third parties without you knowing.
One emerging threat from spyware is the information harvested from the computer can be used in other types of attacks that require a level of social engineering, such as targeted phishing and Denial of Service attacks.
If your device is experiencing any of the following symptoms, you might have spyware:
- Degraded performance
- Random advertisements that pop up on your computer
- Odd behaviour in Internet Explorer or other browsers, such as re-direction to search sites that you've never seen, or your homepage has been switched to a different page.
These can be introduced to a computer by several means for example:
- Connecting an infected external drive to your machine (USB memory stick or external hard drive)
- Downloading an infected file from the Internet
- Clicking on a link supplied in a phishing email
- Downloading and opening an infected email attachment.
